Developers find themselves in
a situation in which they have to secure code through Obfuscation — a term
that is defined as "technique to complicate code so that they are hard to
be reverse-engineered". Although .Net
assemblies are the easiest to be hacked, on a lighter note, someone also said: "The
only things that hackers don’t get are the comments!"
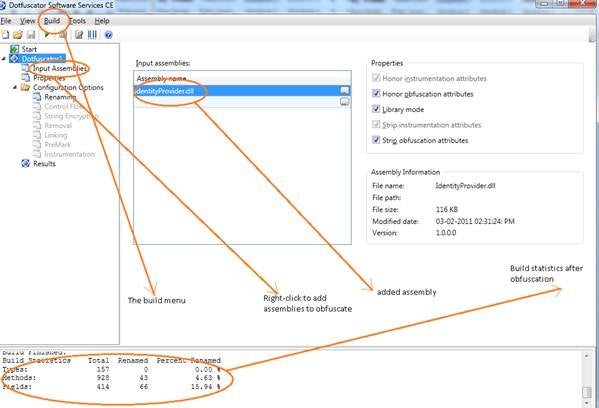
Visual basic developer
center also hosts a series of videos in this regard.
Thanks for reading!
References:
Thwart Reverse Engineering of Your Visual Basic .NET or C# Code


