Because .NET 5 and the .NET 6 preview were released quite close to one another, I thought it would be good to highlight each Framework’s improvements and new features.
.NET 5 Improvements and new Features
Let’s start with .NET 5.
Merged platforms
Microsoft has always had a unified platform vision of a .NET ecosystem. This means that you can use one set of APIs or tools to target a broader set of application types. With .NET 5, you only have to choose the parts of the .NET platform that you’d like to use, without the need to install any other bloated .NET features.
C# 9 changes
This is probably the most important one! .NET 5 includes C# 9 as well as F# 5. Here are a few C# 9 features included in .NET 5 onwards.
C# – Logical patterns
With C# 9 you can combine patterns with logical operators. These are and, or and not. Do not be confused with the operators! If you are struggling with C#, visit the TechRepublic Academy! Here is an example of what I mean:
Student s when s.Age switch
{
>= 18 and <= 80
},
Student in the above example is a class and Age is a property of it. Here the code combines two relational patterns.
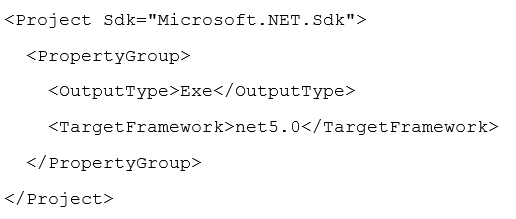
.NET 5.0 Target Framework
A project that targets .NET 5 will have a project file that looks like the following:
Native Code improvements
There are a lot of improvements in working with native code in .NET 5. Here are a few.
ComWrappers
.NET 5 introduces ComWrappers as a way for third parties to generate custom wrappers.
Unmanaged Keyword with Function Pointers
Function pointers in C# 9.0 allow for creating declarations with an unmanaged calling convention simply by using the unmanaged keyword.
delegate* unmanaged<int, int>;
Support for the dynamic keyword in COM objects
.NET 5 includes support for the dynamic keyword and COM objects.
Logging
A custom ConsoleFormatter can be implemented inside the Microsoft.Extensions.Logging library for greater control over formatting and colorization of the console output. .NET 5 also includes a built-in JSON formatter for structured JSON logs in the console.
dotnet-runtimeinfo
With dotnet-runtimeinfo you can print environment information. To install it, open the Developer Command Prompt window and enter:
dotnet tool install -g dotnet-runtimeinfo
To run the tool, enter:
dotnet-runtimeinfo
ClickOnce support
Support for ClickOnce has been added to .NET Core 3.1 and .NET 5.0 Windows apps. It has a familiar look and feel in Visual Studio and a modern CI/CD for ClickOnce publishing with command-line flows, with either MSBuild or the Mage tool.
.NET 6 Preview Improvements and new Features
What are the major improvements in .NET 6 Preview?
.NET Multi-platform App UI
.NET 6 Preview 1 introduces the first two platforms of .NET Multi-platform App UI and they are Android and iOS. Future previews of .NET 6 will add support for macOS and Windows desktop.
To have a look at the sample projects and installation instructions, have a look here.
Arm64
For Windows, Microsoft added support for Windows Presentation Framework and Windows Forms apps, with initial support in Preview 1. For Mac, Microsoft added support for native and simulated Apple Silicon (Arm64) chips, also with initial support in Preview 1.
Portable Thread Pool
The .NET thread pool has been re-implemented as a managed implementation in .NET 6. This is now the default thread pool in .NET 6 and the standard for .NET going forward.
Crossgen2
Crossgen2 replaces the old crossgen tool. Crossgen2 enables cross-compilation across operating systems and architecture dimensions. This simply means that you will be able to use a single build machine to generate native code for all targets.
Hardware-accelerating structs
In .NET 5 and .NET 6, Microsoft has been improving performance for structs so that they can be loaded and accessed in CPU registers. The following struct changes are included in Preview 1:
Blazor Desktop Apps
Blazor has been extended to enable you to write Blazor desktop apps. This empowers developers to create hybrid client apps that combine web and native UI together in a native client application.
New Math APIs
.NET 6 will include new performance-oriented math APIs in the System.Math namespace. These new System.Math APIs are:
-
SinCos
-
ReciprocalEstimate
-
ReciprocalSqrtEstimate
Let’s have a closer look at each.
SinCos
SinCos allows you to compute Sin and Cos simultaneously, as Sin and Cos often need to be calculated together.
Its signature in System.Math would look like:
public (double Sin, double Cos) SinCos(double x);
Its signature in System.MathF would look like:
public (float Sin, float Cos) SinCos(float x);
ReciprocalEstimate
ReciprocalEstimate computes an approximation of 1 / x.
ReciprocalSqrtEstimate
ReciprocalSqrtEstimate computes an approximation of 1 / Sqrt(x).
Fast Inner Loop
The goal of the Fast Inner Loop project is to make the build run faster, creating systems to skip the build altogether, and enabling code edits to be applied to a live process without having to restart it (Hot Reload).